If you are working in the telecom field, I think it is rare that you don’t work with Wireshark to capture the network or open the tcpdump outputs. Although, as a developer, you need to use the reference packet captures, to see the correct packet flow and structure for a specific protocol while you are implementing (if you couldn’t find a reference pcap, you will be walking in the darkness!)
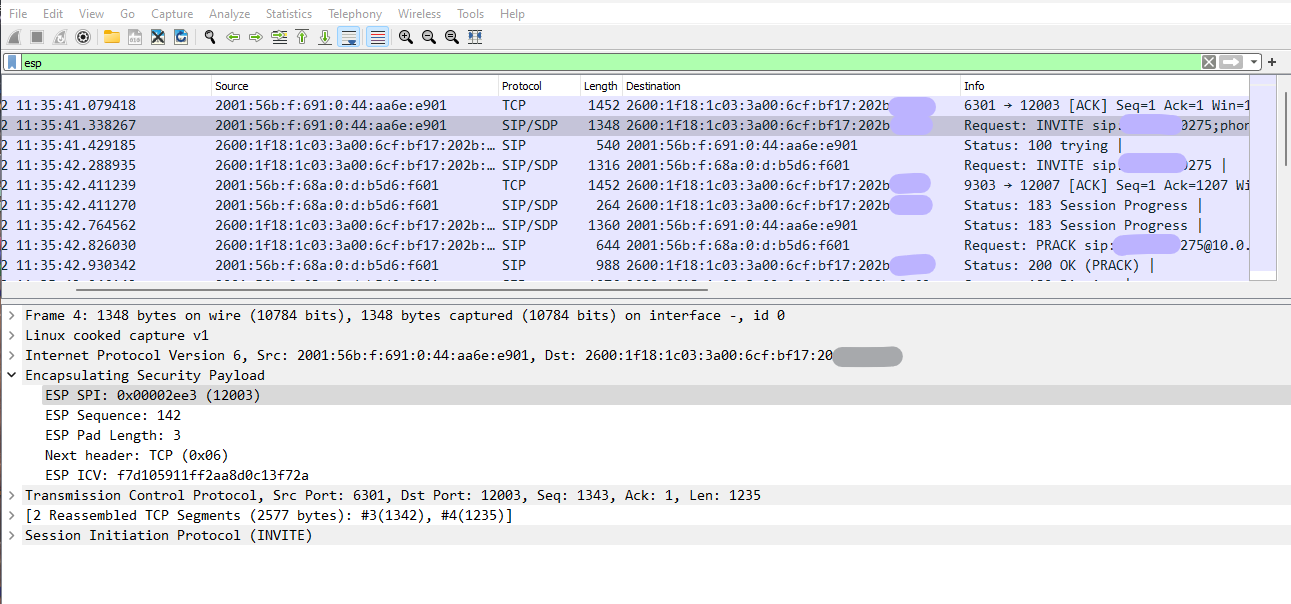
In the VoLTE network or IMS, subscribers use Internet Protocol Security (IPSec) tunnels to connect to the IMS core. In another word, the Gm interface between subscribers (UEs) and the P-CSCF server is secured with IPSec. I will go through IPSec details in another post, but for now, if you have an IPSec capture, you can see a bunch of Encapsulating Security Payload (ESP) packets that their content is not visible.
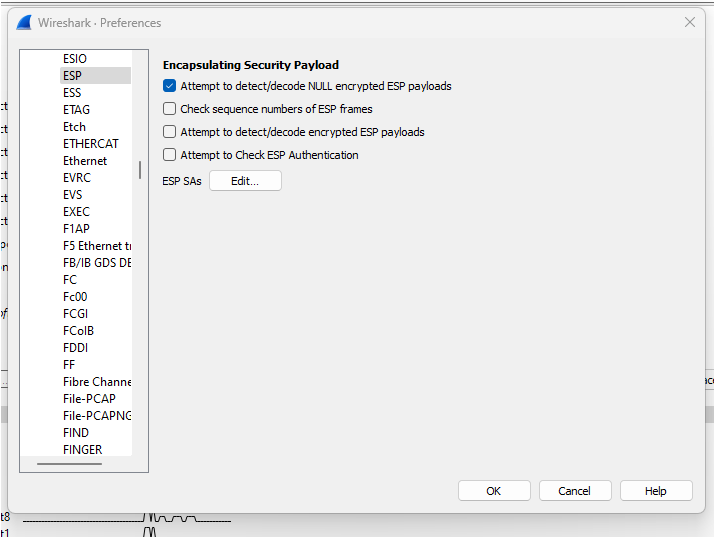
IPSec can be used for integrity or integrity and ciphering; in the first mode, there isn’t any encryption on ESP and you can decode it easily. For this purpose just open preferences settings in Wireshark and for ESP protocol, check the first setting:
- Edit -> Preferences -> Protocol -> ESP
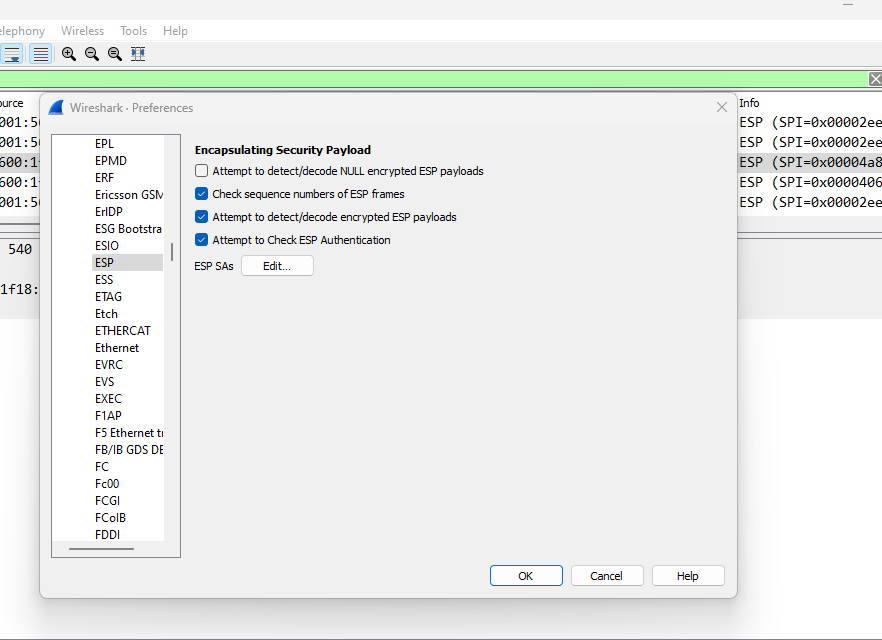
If subscribers or operator forces for ciphering, ESP packets are encrypted and you need more info to decrypt them. In this case, you need to follow below steps:
- Go to same settings: Edit -> Preferences -> Protocol -> ESP
- Select 3 checkboxes (not the first one!) and select ‘Edit’ next to ESP SAs:
- Create an entry for the each IPSec SAs and add the information obtained from the P-CSCF for IPSec tunnel:
-
Protocol: IPv6 or IPv4
-
Src IP and Dst IP: UE IP and P-CSCF address
-
SPI: eg. 0x7bfa58a1
-
Encryption: AES-CBC [RFC3602] (or whatever is selected for IPSec tunnel)
-
Encryption Key: 0xCK
-
Authentication: HMAC-SHA-1-96 [RFC2404] (or whatever is selected for IPSec tunnel)
-
Authentication Key: 0xIK
CK and IK are ciphering and integration keys, that you can find from tunnel information on P-CSCF or before removing them from SIP 401 response to subscriber REGISTER.
Now, you can see the ESP content: