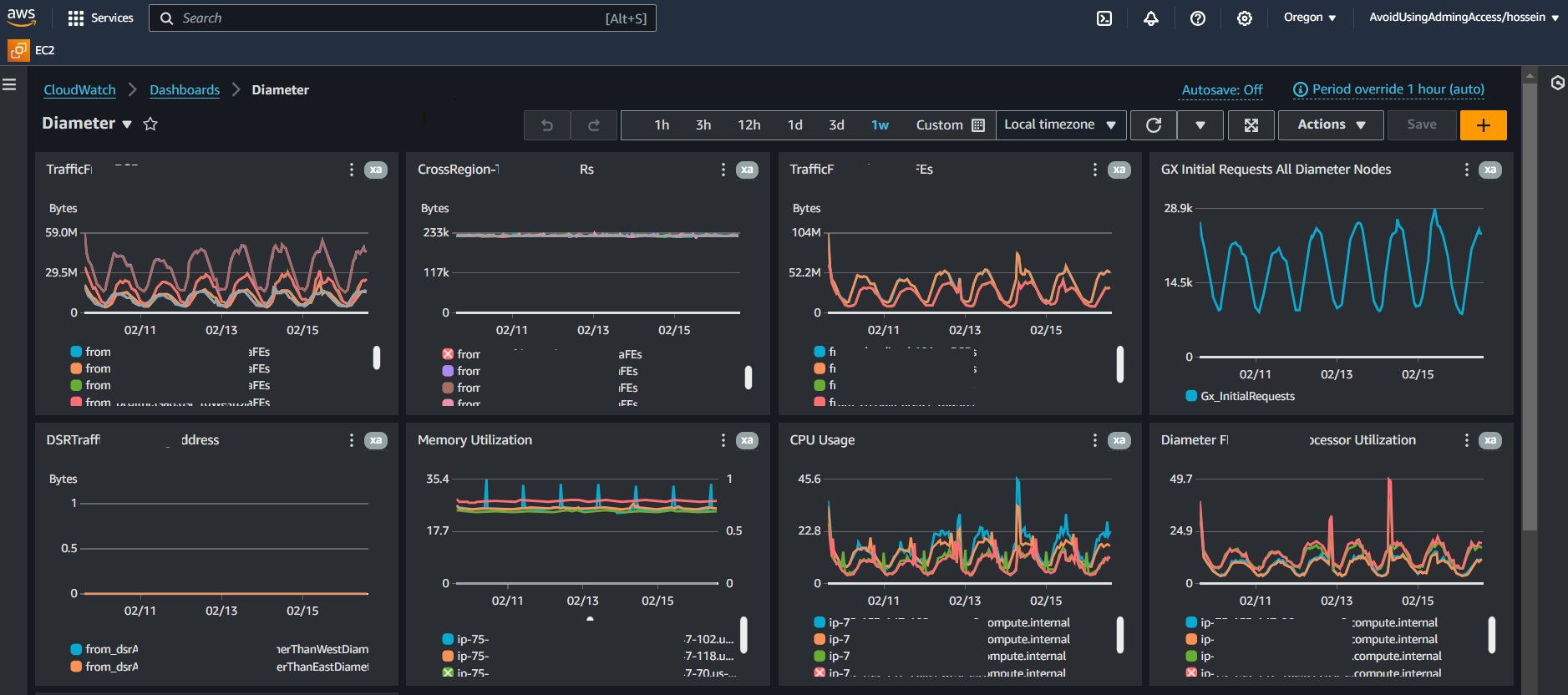
Yesterday, I successfully configured distinct metric filters for specific CloudWatch log groups within our AWS lab environment. After verifying their effectiveness, I realized the need to replicate these filters across both our AWS staging and production environments.
** I understand that AWS CloudWatch offers cross-account capabilities, but let’s assume for a moment that utilizing them isn’t feasible or recommended, as was the case in my situation. Additionally, there are instances, like mine, where swiftly integrating your CDK and deployment process to accommodate these requirements may not be feasible. While it’s true that log group metric filters can be added through AWS CDK during the deployment phase, implementing such changes entails additional steps and approvals for staging and production updates. Nevertheless, I wanted to highlight that my solution could potentially offer a time-saving alternative in certain scenarios.
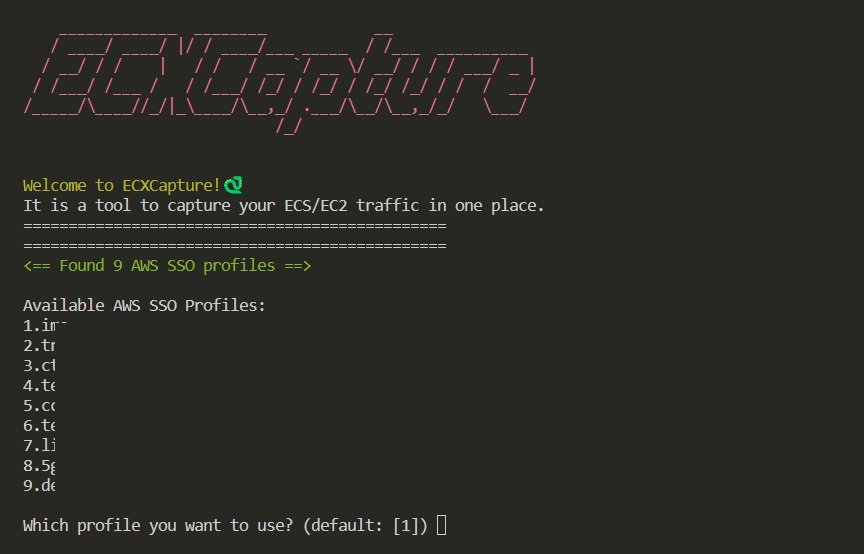
I’ve recently developed a straightforward yet, in my opinion, a quite handy tool for network troubleshooting. This tool simplifies the process of obtaining tcpdump from your AWS ECS tasks or EC2 instances directly from your desktop, all in one place!
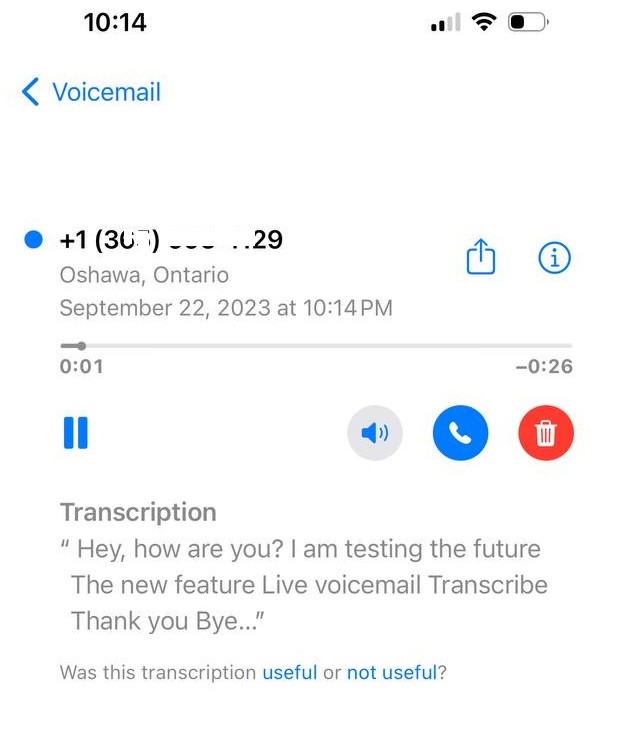
Probably you have updated your iPhone iOS recently to version 17 and the only thing that in the first place you have recognized, it was the phone screen when someone calls you. You can find a Voicemail icon that represents the new Live Voicemail feature.
 Caption: Photo courtesy of John Downer Productions
Caption: Photo courtesy of John Downer Productions
Lawful Interception (LI) standard play a crucial role in enabling lawful interception activities by authorized entities for security and intelligence purposes. These protocols allow the interception and monitoring of communication services while adhering to legal requirements. If you’re involved in IMS/mobile core or other telephony networks development, or communication analysis and security, you’ll find a dissector besides Wireshark be an invaluable addition to your toolkit. In this blog post, I’ll introduce you to x2x3PduDissector, a powerful Lua-based Wireshark dissector for analyzing LI (X2/X3 PDU Format) packets.

If you are testing an NG911 IMS call, one of the most important pieces of info that the NG911 network (including LRF, NGCS, PSAP, …) expects from your SoS SIP INVITE is the P-Access-Network-Info or PANI header. This header carries the information about the UE/Subscriber device location.



 Caption: Photo courtesy of John Downer Productions
Caption: Photo courtesy of John Downer Productions